4: Data and Posture Baseline Lifecycle (DPBL)#
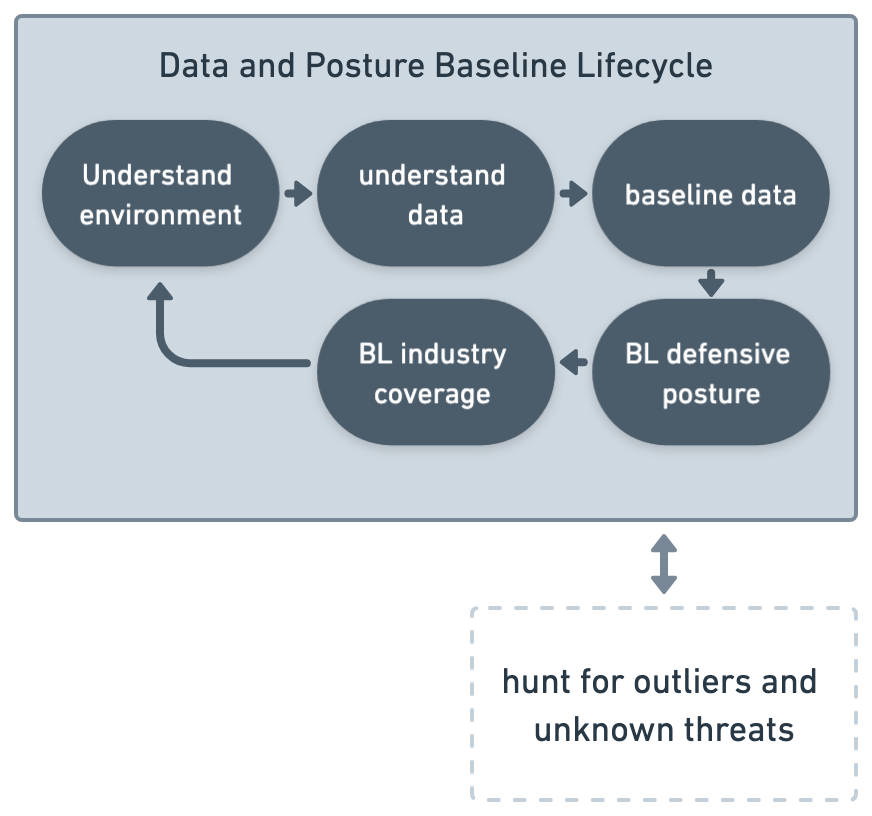
Fig. 3 DPBL#
DPBL outlines the steps that are required for an overall successful detection engineering operation. Because of an ever changing internal environment and external threat landscape, it is worth the investment in time to master this step.
Chapter 2 discussed the differing perspectives and how they impact considerations and decisions within detection engineering. This is a primary example of such a scenario, which identifies important concessions to be made and understood. Product teams building content for a diverse population of customers cannot simply just use their enterprise environment as the sole reference, because doing so could unintentionally create environmental bias, where the output is overfitted.
For a security operations organization, such as an internal security team or an MSSP, this exercise would be based on their environments in order to build the context and frame the rest of their detection engineering processes around it. As such, it is necessary to adopt a conceptual environment to drive efforts. This pseudo-environment should be an amalgamation of the perception of standard environments based on reference architectures, awareness of any internal or customer-specific environments, and observations from any incoming customer telemetry.
