1e. Baseline industry threat coverage#
This step focuses on consuming existing threat information from across the industry to derive valuable insights, especially those most relevant to the specific environment. There are countless blogs and publications that provide invaluable information across many technologies, threats, and actors.
Elastic Security Labs is one such resource, known for consistently releasing high quality first party security research. In addition to research on many different topics, you can also find detection rules for SIEM, behavioral rules for EDR, YARA signatures, and ransomware artifacts — all shared openly with the community. All of these artifacts are the outcome of very mature and advanced detection engineering principles largely reflected within this publication.

Fig. 7 Elastic Security Labs research articles#
Another common medium for sharing research and insights are recurring threat reports, which focus on observations at a grander scale. The Elastic Global Threat Report is a prime example of this and a great resource to consult. You can find similar reports across the industry from various vendors and projects, all providing unique perspectives and insights.

Fig. 8 Elastic 2023 Global Threat Report contents#
The development of shared or open rules and signatures has seen an uptick in recent years. They are coming from multiple sources as well, including vendors, open source projects, and individuals, driving this trend of community collaboration for detection engineering efforts.
In addition to Elastic’s EDR and SIEM rules, other vendors openly sharing include Splunk, Microsoft, and Google Chronicle. Open source projects such as Sigma provide platform-agnostic rules and an ecosystem for sharing and collaborating. There are even several significant individual efforts such as Bert-Jan’s project, which shares Defender For Endpoint & Microsoft Sentinel Kusto rules.
Fig. 9 Elastic SIEM rules repo#
Ways to take advantage of this data in order to baseline industry threat coverage include:
Review security blogs and threat reporting
Review security artifacts such as rules and signatures openly shared
Follow curated Twitter feeds
Review source code of open security projects
Review issues, pull requests, and discussions in GitHub and other sources repositories
Review documentation for relevant security products and projects
Peruse and study bug bounty reports
Review CVE database and details
Stay updated on Mitre ATT&CK and sister projects
As a means to more conveniently derive insights and observations from these open rule sets, along with helping baseline them to establish an observed industry standard, I recently released an open source project, which consumes several of the major rule sets, along with development metadata, and presents it in an Elastic stack for easy searching and visual analysis. This project is called REx: rule explorer, and the details can be found in the release blog.

Fig. 10 REx: Rule Explorer breakdown of ATT&CK techniques across rule sets#
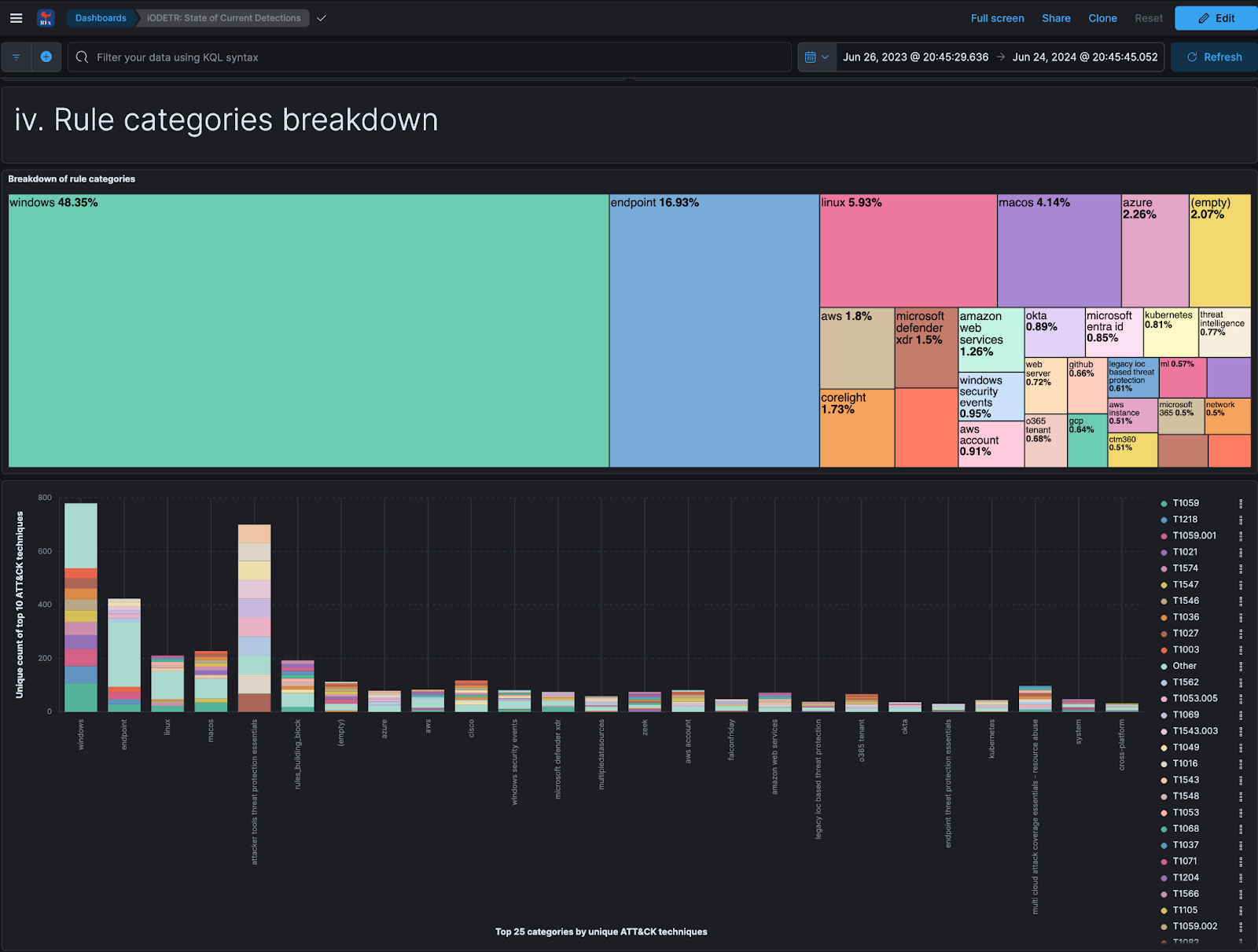
Fig. 11 REx: Rule Explorer breakdown of threat categories across rule sets#
We will leverage the REx: rule explorer project for other things, such as building new metrics, throughout this publication as well.
