3c. Release | activate#
At this step, product teams will focus on releasing rules, whereas operational teams would most likely focus on activating them within their environments. Most security vendors try to release security content updates out of band from their normal feature development cycles. This is especially necessary due to the fast and volatile nature of the threat landscape. If releasing out of band, it will usually involve the intermediate use of a CDN to decouple the release from directly going to user environments (though they may immediately pull them once available).
Releasing should involve specific testing for any additional steps involved. A good release process will also allow users the ability to configure how the updates are pulled in. This can either be from a configuration policy or perhaps a UX workflow.
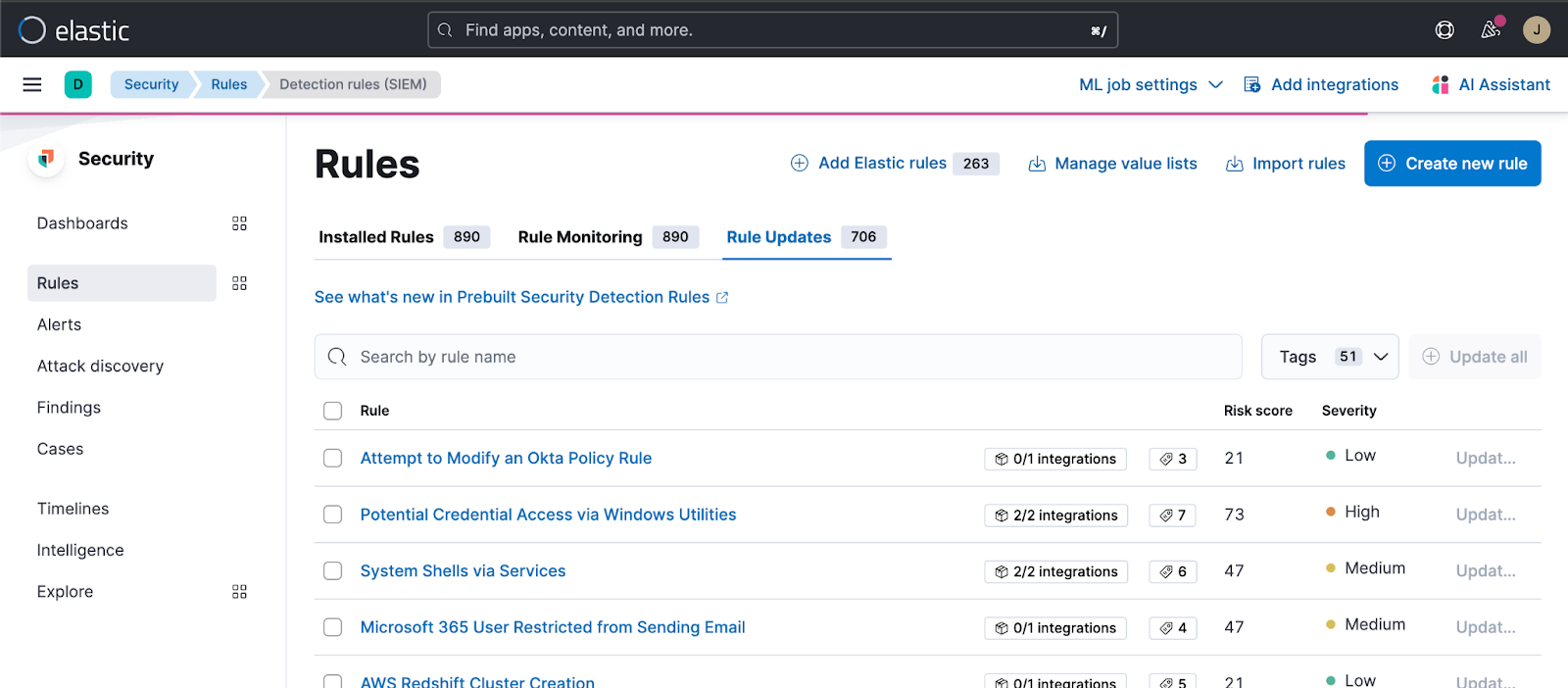
Fig. 37 Elastic security interface for granular acception of new rule updates#
A few good practices with releases are to include a good changelog as well as to keep documentation updated. Linking to the source of the changes, such as a rules repo is also very helpful, as it allows users to understand the changes. Even better, would be to incorporate an interface that shows the deltas of the changes in a syntax highlighted, interactive workflow within the platform, such as within Kibana.
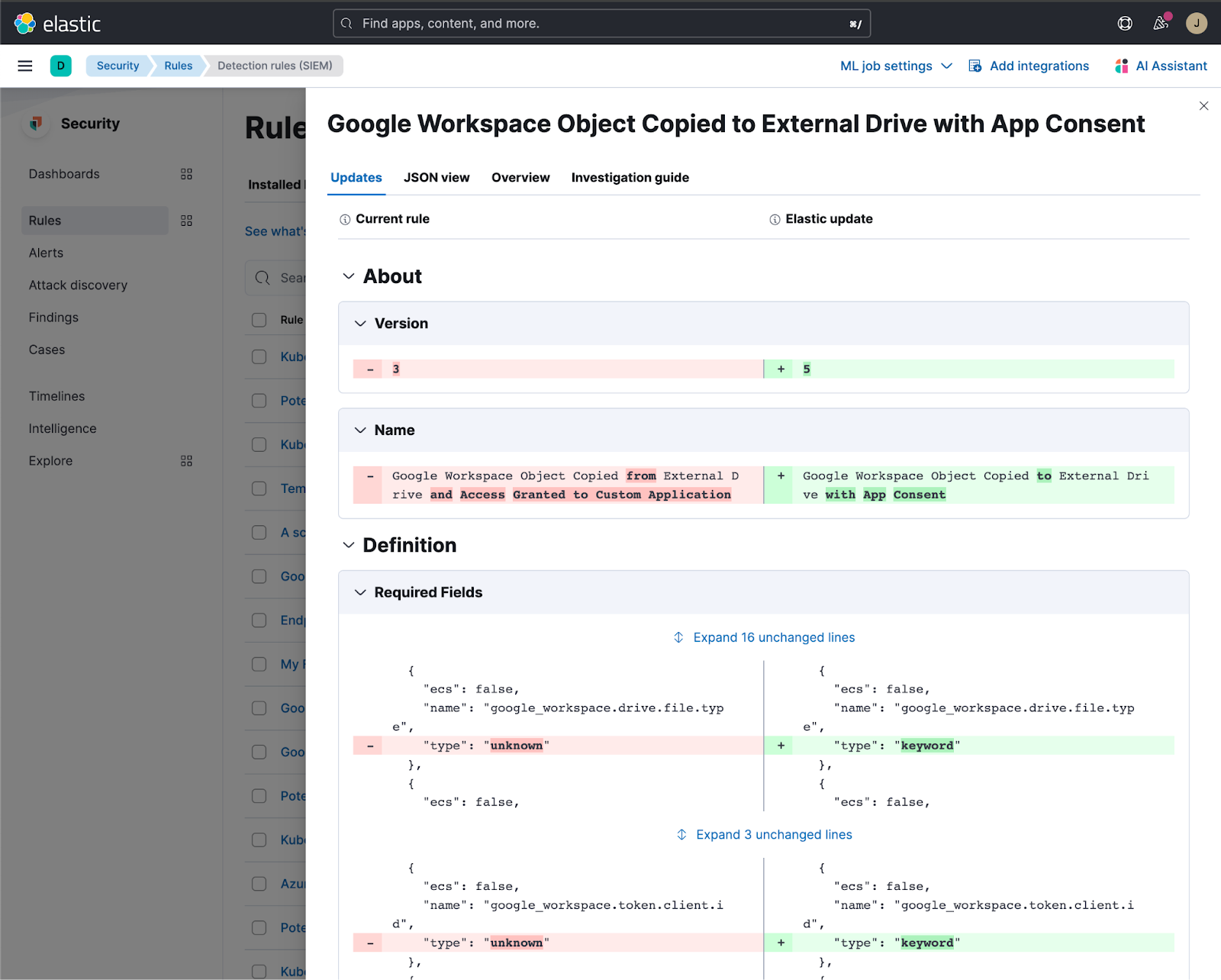
Fig. 38 Elastic security rule update showing detailed changes#
This brings us to the important topic of change management. This applies to operational teams as well, whether they are incorporating upstream vendor updates, or activating new rules internally developed. Issues tend to arise more with the latter situation, since change management tends to be poorly adopted and implemented, and it seems worse with regard to SIEM rules specifically.
It is not uncommon for users to simply accept all the changes without reviewing and verifying or testing them. Ironically, multiple updates may even frustrate users in this process, since it would require them to integrate even more changes, even though the volatility of the rules may be to adapt to a changing threat landscape.
Regardless of the concerns or lack of resources, a mature change management program should absolutely be in place and exercised with all changes whenever possible.
